![]()
There have been recent reports of a worrying cyberattack known as “Apple ID push bombing.” This exploit sends a deluge of spam reset notifications directed at iPhone users in particular. The assault seeks to cause annoyance and frustration by inundating users with a deluge of notification messages. Now let’s explore this attack’s details and how users might lessen its effects:
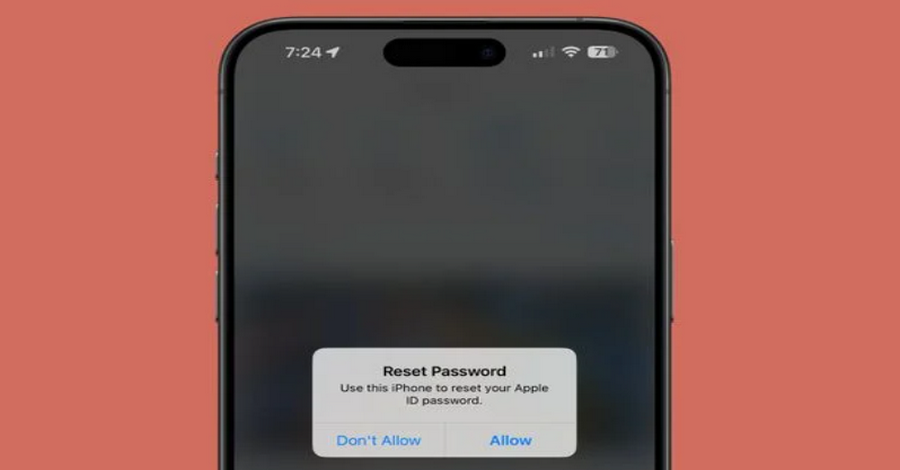
assault Type: A high number of password reset notifications are sent to specific iPhone users as part of an Apple ID push bombing assault. Usually, users may find, lock, or wipe their iPhones remotely by using the “Find My iPhone” feature, which is how these notifications are received. By abusing this function, attackers can bombard users’ smartphones with notifications all the time, which can be annoying and disruptive.
Goal: It seems that the main intention behind this attack is to cause disruption instead of physical injury. Attackers hope to incite chaos, inconvenience, and aggravation by flooding users with spam that contains reset notice links. The assault can negatively affect user experience and productivity even while it doesn’t directly breach users’ personal information or devices.
Method of Execution: The attackers use automated tools or scripts to deliver a large number of password reset reminders to Apple IDs that they have targeted. These notifications, which seem like valid reset requests, inundate users’ smartphones. Users find, however, that the requests are part of a concerted attack and are not permitted after further examination.
Users may become frustrated and perplexed due to the constant barrage of reset notifications. When users are unable to distinguish between dangerous and genuine notifications, their worry and doubt about the security of their accounts may increase. The attack also interferes with users’ regular use of their devices by continuously barraged with notifications, which makes it difficult to accomplish activities efficiently.
Techniques for Mitigation:
It is advisable for users to proceed with caution in the event that they receive unexpected or suspicious password reset messages. Simply put, ignore them. Users should avoid acting or clicking on links in notifications if they are doubtful about their legality. Instead, they should use formal channels to confirm the request’s legitimacy.
Turn Off Locate My Notifications on iPhone: Users may choose to disable Find My iPhone notifications as a temporary solution to lessen the impact of the attack. By doing this, the flood of reset notifications can be avoided until the problem is fixed.
Report and Stop Assailants: If a user receives an Apple ID push bombing assault, they should report it to Apple and remove any linked emails or contacts from the sender. This assists in halting additional harassment and permits Apple to look into and deal with the offenders as necessary.
Remain Informed: It’s important for users to remain aware of new security flaws and potential threats targeting Apple products. Device security and resilience against assaults can be improved by regularly updating firmware and software, creating strong account passwords, and turning on two-factor authentication.
Apple’s Reaction: Apple is alert to the attack using a fake Apple ID and is looking into it. In order to protect consumers from these kinds of malicious activity, the firm is trying to resolve the issue. To lessen the effects of the attack and improve the security of its ecosystem, Apple might provide security upgrades or take additional steps.
The Apple ID push bomber attack, in conclusion, emphasizes the significance of alertness and preventative security measures in defending against cyber attacks. Users can lessen the effects of such assaults and safeguard their devices and private data by being educated, being cautious, and adhering to best practices for account security.
